
Top tips for your business password policy
Roman Cuprik, content writer at ESET explains that don’t torture people with exceedingly complex password composition rules but do blacklist commonly used passwords, plus other ways to help people help themselves – and your entire organization
 When engineer Bill Burr from the U.S. National Institute of Standards and Technology (NIST) wrote in 2003 what would soon become the world’s gold standard for password security, he advised people and organizations to protect their accounts by inventing long and ‘chaotic’ lines of characters, numbers, and signs – and to change them regularly.
When engineer Bill Burr from the U.S. National Institute of Standards and Technology (NIST) wrote in 2003 what would soon become the world’s gold standard for password security, he advised people and organizations to protect their accounts by inventing long and ‘chaotic’ lines of characters, numbers, and signs – and to change them regularly.
Fourteen years later, Burr admitted that he regretted his past advice. “It just drives people bananas and they don’t pick good passwords no matter what you do,” he told the Wall Street Journal.
Or, as the famous xkcd comic has put it: “Through 20 years of effort, we’ve successfully trained everyone to use passwords that are hard for humans to remember, but easy for computers to guess.”
These days, an average person has up to 100 passwords to remember, with the number growing at a rapid clip in recent years (although in fact, some people used around 50 passwords, including a number of offline codes, even years ago and some security experts have been pointing out that such password habits and policies are unsustainable.)
Indeed, studies have found that people typically remember just up to five passwords and take shortcuts by creating easy-to-guess passwords and then recycle them across various online accounts. Some may actually substitute numbers and special characters for letters (e.g., “password” turns into “P4??WØrd”), but this still makes for a password that is easy to crack.
In recent years, leading organizations such as The Open Web Application Security Project (OWASP) and, of course, NIST itself have shifted their policies and advice towards a more user-friendly approach – all while increasing password security.
At the same time, tech giants such as Microsoft and Google are encouraging everyone to ditch passwords altogether and go passwordless instead. However, if your small or medium-sized business isn’t ready to part ways with passwords just yet, here’s some guidance that will stand you and your employees in good stead in 2023.
Stop imposing unnecessarily complex password composition rules
Any exceedingly complex composition rules (such as requiring users to include both uppercase and lowercase characters, at least one number and a special character) are no longer a must. This is because such rules rarely encourage users to set stronger passwords, prompting them instead to act predictably and come up with passwords that are a “double whammy” – they’re both weak and difficult to remember.
Switch to passphrases
Instead of shorter but difficult passwords, go for passphrases. They are longer and more complex but still easy to remember. For example, it may be a whole sentence that stuck in your head for some reason, sprinkled by capitals, special characters, and emojis. While not being super complex, it will still take ages for automated tools to crack it.
A few years ago, the minimum length for a good password was eight characters, which consisted of lower and upper cases, signs, and numbers. Today, automated password cracking tools can guess such a password in minutes, especially if it’s secured with the MD5 hashing function.
This is according to tests run by Hive Systems and published in April 2023. On the contrary, a simple password that contains only lower and upper case characters but is 18 characters long takes far, far longer to crack.
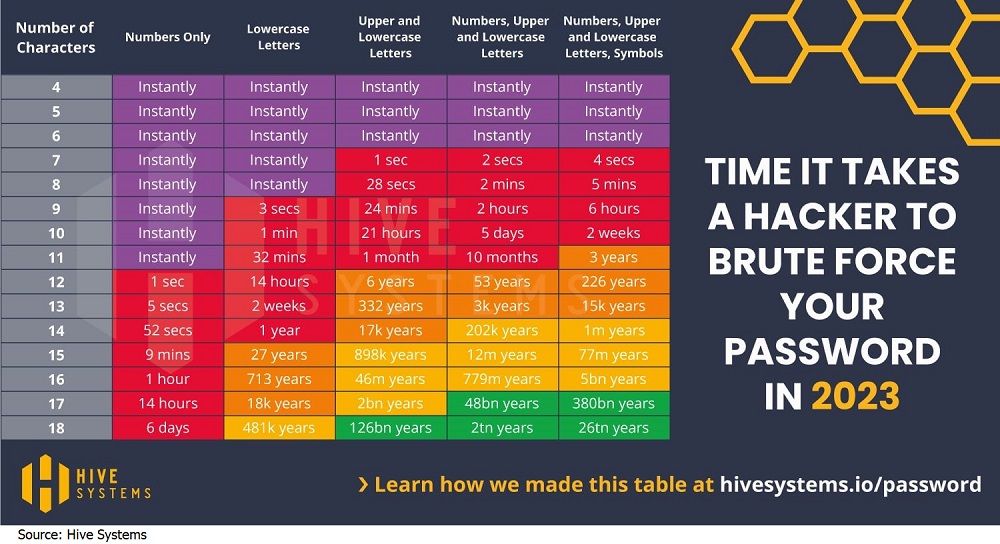 Aim for a minimum length of 12 characters – the more the better!
Aim for a minimum length of 12 characters – the more the better!
The NIST guidelines acknowledge length as the key factor in password strength and introduce a minimum required length of 12 characters reaching up to a maximum of 64 characters after combining multiple spaces. All things being equal, the more the merrier.
Enable a variety of characters
When they set their passwords, users should be free to choose from all printable ASCII and UNICODE characters, including emojis. They should also have the option to use spaces, which are a natural part of passphrases – an oft-recommended alternative to traditional passwords.
Clamp down on password reuse
It’s conventional wisdom by now that people shouldn’t reuse their passwords across different online accounts, because a breach of one account can easily lead to the compromise of other accounts.
However, many habits die hard, and around half of respondents in a 2019 Ponemon Institute study admitted to reusing an average of five passwords across their business and/or personal accounts.
Don’t set a “use by” date for passwords
The NIST also recommends against requiring regular password changes unless requested by the user or unless there is evidence of a compromise. The rationale is that users only have so much patience for having to constantly think of new reasonably strong passwords. As a result, getting them to do so at regular intervals can do more harm than good.
When Microsoft announced dropping the password expiration policies three years ago, it questioned the whole idea of password expiration.
“If it’s a given that a password is likely to be stolen, how many days is an acceptable length of time to continue to allow the thief to use that stolen password? The Windows default is 42 days. Doesn’t that seem like a ridiculously long time? Well, it is, and yet our current baseline says 60 days – and used to say 90 days – because forcing frequent expiration introduces its own problems,” reads Microsoft’s blog.
Keep in mind that this is just general advice. If you are securing an app that is crucial for your business and attractive to attackers, you can still force your employees to change passwords periodically.
Ditch hints and knowledge-based authentication
Password hints and knowledge-based verifying questions are also obsolete. While these might in fact help users on their search for forgotten passwords, they can also be of great value for attackers. Our colleague Jake Moore has shown on several occasions how hackers can abuse the “forgotten password” page on in order to break into other people’s accounts, for example on PayPal and Instagram.
For example, a question such as “your first pet’s name” can be easily guessed with a little bit of research or social engineering and there is not really an endless number of possibilities that an automated tool has to go through.
Blacklist common passwords
Rather than rely on previously used composition rules, check new passwords against a “blacklist” of the most commonly used and/or previously compromised passwords and evaluate matching attempts as unacceptable.
In 2019, Microsoft scanned its users’ accounts comparing the usernames and passwords to a database of more than three billion sets of leaked credentials. It found 44 million users with compromised passwords and forced a password reset.
Provide support for password managers and tools
Make sure that the “copy and paste” functionality, browser password tools, and external password managers are permitted to handle the hassle of creating and safekeeping users’ passwords.
Users should also choose to either temporarily view the entire masked password or the last typed character of the password. According to the OWASP guidelines, the idea is to improve the usability of credential entry, particularly around the use of longer passwords, passphrases, and password managers.
Set a short shelf life for initial passwords
When your new employee establishes an account, the system-generated initial password or activation code should be securely randomly generated, at least six characters long, and may contain letters and numbers.
Make sure that it expires after a short period of time and cannot become the true and long-term password.
Notify users about password changes
When users change their passwords, they should be asked to first enter their old password and, ideally, enable two-factor authentication (2FA). Once done, they should receive a notification.
Be careful about your password recovery process
Not only should the recovery process not reveal the current password but the same also applies to information on whether the account actually exists or not. In other words, don’t provide attackers with any (unnecessary) information!
Use CAPTCHA and other anti-automation controls
Use anti-automation controls to mitigate breached credential testing, brute force, and account lockout attacks. Such controls include blocking the most common breached passwords, soft lockouts, rate limiting, CAPTCHA, ever-increasing delays between attempts, IP address restrictions, or risk-based restrictions such as location, first login on a device, recent attempts to unlock the account, or similar.
According to the current OWASP standards, there should be at most 100 failed attempts per hour on a single account.
Don’t rely only on passwords
Regardless of how strong and unique a password is, it remains a single barrier separating an attacker and your valuable data. When aiming for secure accounts, an additional authentication layer should be considered as an absolute must.
That is why you should use two-factor (2FA) or multi-factor authentication (MFA) whenever possible.
Not all 2FA options are born equal, however. SMS messages, while far better than no 2FA at all, are susceptible to numerous threats. More secure alternatives involve using dedicated hardware devices and software-based one-time password (OTP) generators, such as secure apps installed on mobile devices.
